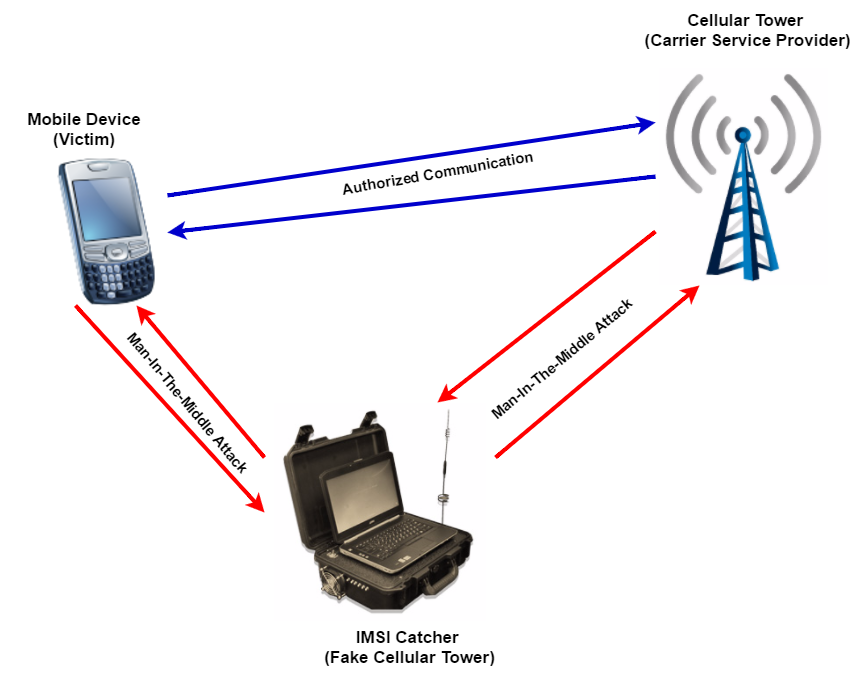
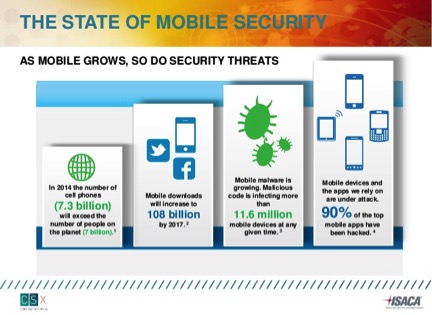
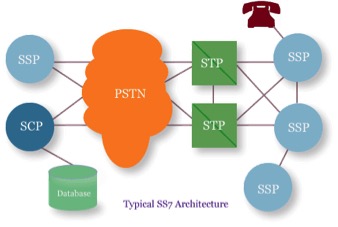
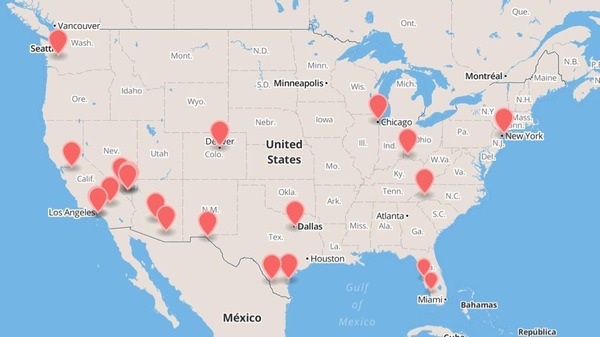
The Threat
Man-in-the-Middle (MITM) mobile attacks can be accomplished in a wide range of technical ways, but the high level effect is the same in every scenario. An individual manages to insert himself between a call originator and recipient, and manages, as well, to fool each party into believing they are communicating directly with the other desired party, when, in fact, they are each communicating with the attacker. Having thus convinced each party that they are taking part in a legitimate and secure conversation, the attacker then has access to both parties’ IMSI numbers, physical locations, and all of the contents of their conversation, which can, in turn, be eavesdropped on or recorded for other nefarious purposes.
How Does It ...